Vendor comparison of the largest LPWAN standards with a view to IT security and cryptography
Within the framework of the basic technology LPWAN, various radio standards have been produced by manufacturers and committees. NB-IoT, LTE-M, LoRaWAN, Sigfox and Weightless deserve special mention here. In our blog post " Deploying advanced LPWAN technology in water supply networks to reduce water loss: why? And what does it have to do with IoT?", the advantages of LPWAN technology over traditional methods have already been highlighted. But the question remains as to which LPWAN standard is most appropriate for a water supply network. Only one research paper on Low Power Wide Area Network (LPWAN) systems in a water supply system could be found. The paper "Smart Water Grid Management using LPWAN IoT Technology" only describes that LoRaWAN has been identified as the best technology without explaining other LPWAN standards and their evaluation process. It is also not clear why LoRaWAN should be better than other LPWAN standards under consideration and what these are in detail.
In this blog post, the largest and most suitable LPWAN standards will be explained and compared and evaluated based on evaluation criteria. For this purpose, investigation processes and results from the master thesis of Waldemar Heinrich (Head of Process Informatics, narzsystems GmbH & Co. KG) "Evaluation of LPWAN standards, their IT security requirements and technical designs for integration into a planned Smart Water Grid" will be used.
Evaluation criteria
Individual explanations for the subsequent evaluation criteria now follow this section. The importance of the parameters for the upcoming comparison is to be emphasized.
Costs and freedoms
An LPWAN system can be divided into two categories of cost items. One of them refers to the pure acquisition of hardware (LPWAN modules, antennas). The other reflects the maintenance costs of the systems in an LPWAN. Batteries and licenses are considered as maintenance costs. Since there is no deployment with fully vendor-dependent LPWANs, there are no possible monthly fees in the maintenance. By complete vendor dependency is meant the service, the network and software for process control. In addition, it is interesting to see what freedoms the various LPWAN standards offer. By freedom, we mean that there may be no hardware lock-in or that the use of protocols is not predefined.
Frequencies and licenses
This category is intended to show the frequencies of the various LPWAN standards and to highlight possible advantages and disadvantages. The frequencies used will be limited to Germany, unless there seem to be possible advantages that show possible international support. At the same time, licensed and free frequencies should always be mentioned. If relevant, the bandwidths used should also be mentioned if they provide important attributes for communication.
Power consumption
One of the most important criteria is the energy requirement in an LPWAN. The name LPWAN already includes the definition of the required minimum energy consumption. Since the energy consumption in the active mode of an LPWAN module depends on many factors and, in the water supply scenario, a data transmission of once per day can be assumed, the energy consumption in inactive mode (sleep mode) must be specified for each LPWAN standard. This appears to be much more important, since the period of inactive mode is much higher compared to active mode (e.g. active mode approx. 1 minute, inactive mode approx. 23 hours and 59 minutes). The comparison of the different LPWAN standards would also be easier to collect, since no special cases or parameters have to be explicitly explained in the inactive state of the modules used.
Range and signal strength
The different ranges and signal strengths of an LPWAN standard are to be compared. The range could be parameterizable, which could possibly have an effect on the signal strength. Furthermore, the reachability of sensors must be illuminated, since in this case the signal strength (sensitivity) can be adjusted via possible controllers or antennas.
Disruptive factors and countermeasures
A radio network is always freely exposed to the environment and thus always susceptible to interference from outside. Possible interference factors are to be named and, if necessary, automatic countermeasures, which are already available in LPWAN standards, are to be shown. These include, above all, automatic detection and handling of malfunctions.
IT security and cryptography
In the KRITIS-V water sector, security is probably the most important issue. The aim is to find out which IT security measures are already supported by LPWAN standards. It should be made clear whether the security measures are already integrated in the standard or can be integrated by additional interfaces and parameters from external solutions. If external solutions exist, they should be assigned to the respective LPWAN standard.
Since there is no longer any IT security without cryptographic encryption, the use or compatibility of established encryption methods should be mentioned. Encryption should consider the communication structure and path, as well as the transmitted or stored data on and from the LPWAN modules and protocols used.
Security must be applied to the entire LPWAN system, but in this comparison of LPWAN standards until the data leaves the LPWAN network.
Evaluation standard
For simplicity, the evaluation scale is composed of the listed values in Table 1.
Table 1: Definition application benchmark
Value | Definition |
1 | The strengths in this criterion are clearly above average |
2 | The strengths in this criterion are good |
3 | The strengths in this criterion are evident, but not good |
4 | The criterion has neither strengths nor weaknesses |
5 | The criterion has recognizable weaknesses |
6 | The criterion has major weaknesses |
Each criterion is given a unique rating. The best evaluation is represented by a 1, the worst by a 6, as is done in a performance evaluation with grades. Finally, an average value is calculated from five of the six evaluated criteria and all the LPWAN standards identified are compared in a table. In a pre-selection of LPWAN providers in advance, some were not included in the upcoming comparison. Basically, the freedoms, the range and the energy requirements were checked and a preliminary decision was made on the basis of these. Table 2 is intended to list all the LPWAN providers considered and show which were included in the comparison and which were not.
Table 2: Preselection of LPWAN providers
Provider | Comparison | Justification |
Sigfox | No | Manufacturer bound |
Ingenu | No | Manufacturer bound |
Telensa | No | Manufacturer bound |
Qowisio | No | Manufacturer bound |
Nwave | No | Manufacturer bound |
IEEE 802.15.4g | No | Low range (WPAN) |
| IEEE 802.15.4g | No | Low range (WPAN) |
EnOcean | No | Low range (WPAN) |
NB-Fi | No | Manufacturer bound |
LoRa / LoRaWAN | Yes | Established standard, active further development |
Weightless | Yes | License free frequencies |
NB-IoT | Yes | Long battery life, Telekom as provider |
LTE-M | Yes | Energy-saving 4G radio chips over LTE |
EC-GSM-IoT | Yes | Energy-saving GSM protocol |
DASH7 | Yes | Similar structure to LoRaWAN |
Furthermore, there are a large number of LPWAN standard providers, but they are not mentioned further.
Comparison and presentation of LPWAN standard providers
All criteria listed above are compared. To provide a better understanding of the individual LPWAN standards, their mode of operation is explained at the beginning and then the assessments are worked through one after the other. The assessment of a criterion is documented directly in the corresponding section. A summary of the assessment of all LPWAN standards can be viewed in the "Final Assessment and Summary of Findings" section.
LoRa/LoRaWAN - Alliance
Long Range Wide Area Network (LoRaWAN) is a transmission technology developed for LPWAN based on a dedicated radio network. The rough attributes are:
• Inexpensive and small sensors
• Battery-powered devices that have a runtime of about 5 to 10 years.
• Devices are optimized to send small data packets at low operating cost.
There is a differentiation in the terms LoRa and LoRaWAN:
• LoRa represents the communication through the transmission layer, which is what makes the long ranges possible in the first place.
• LoRaWAN describes the system architecture of the network. In combination with the communication protocol, the operation of the network is thus energy-saving.
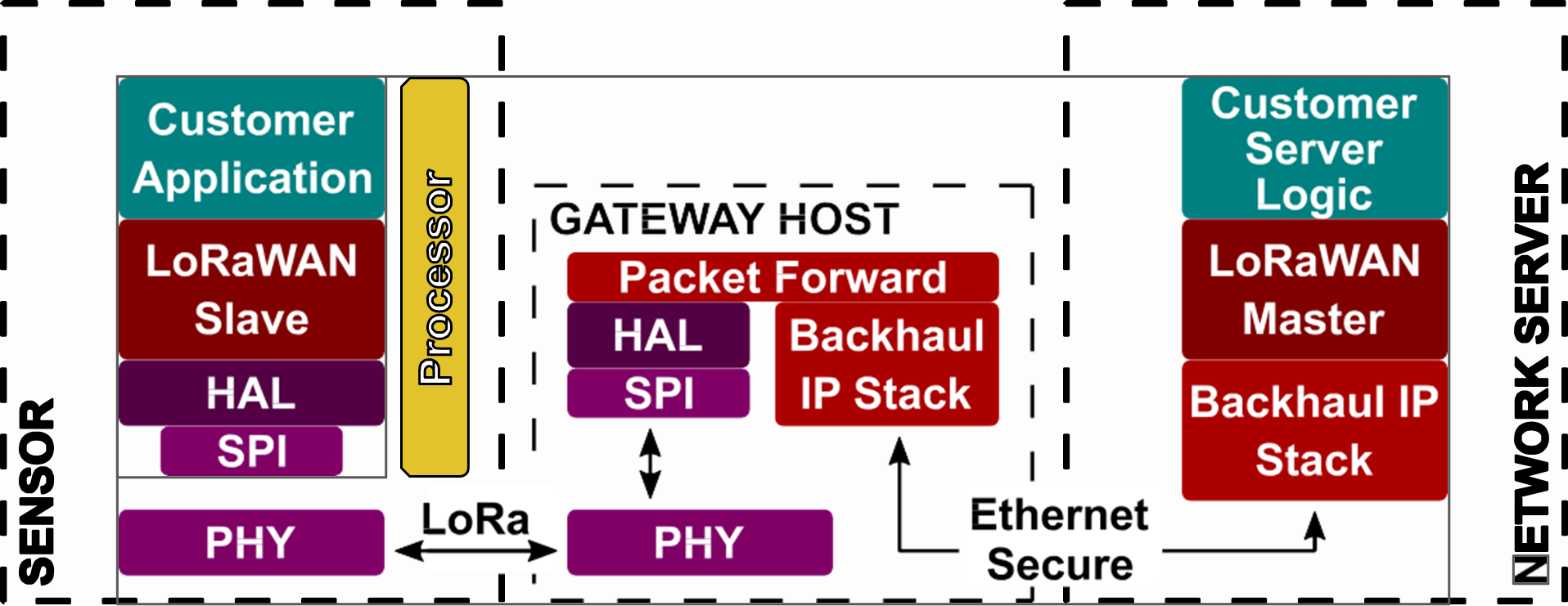
Gateways communicate with their nodes, whereby these are not permanently assigned to just one gateway. These gateways pass on their recorded data via conventional transmissions to the Internet to a cloud or a specified endpoint. To transmit the data, the gateways are given time slots that are activated on an event-driven basis, randomly, or by device class. The data is protected by 128-bit AES encryption. The transmission of the individual bits is routed via the physical layer of the sensors and gateways. Coding and decoding is their main task. Furthermore, both components are equipped with the hardware abstraction layer (HAL), which is used to retrieve the hardware information and enables communication with the hardware.
Costs and freedoms
The cost question can quickly be answered positively in LoRaWAN. For the application in the scenario under consideration, very few sensors are required per site. This makes LoRaWAN an optimal candidate. Because these sensors and gateways were developed precisely for this scenario. In addition, this is exactly where the big advantage of LPWAN technology lies compared to conventional more expensive solutions. The fixed costs of the hardware coincide with other modules, which is why the advantage lies in the maintenance costs. Due to the open radio standard, it is possible to build a LoRaWAN as an IoT network with bidirectional communication.
Rating: 1
Frequencies and licenses
LoRa operates in a free frequency range which is 868 MHz in Europe for bidirectional communication (there are sub-bands in the range from 863 to 870 MHz) and therefore no license costs are necessary. In North America this frequency is 915 MHz and in Asia 433 MHz.
Rating: 1
Power consumption
The LoRa modules are optimized for transmit power at low power consumption. The service life of a battery can be up to 15 years. However, the selected device class is decisive here. In the scenario considered, device class A would have to be selected. Since device class A is the most energy-efficient class, the power consumption is very positive. However, the energy consumption can vary depending on the range to be covered and the transmission speed. Ideally, the bandwidth should be selected at 125 kHz with a spreading factor (SF) of seven. The spreading factor is responsible for the transmission of bit sequences in spread spectrum technology, which is also used by LoRaWAN. The higher the spreading factor, the greater the range, but this also increases the power requirement. It is not possible to give an exact power consumption, since different currents are used depending on the chip type. However, the consumption in standby mode should be mentioned, which is 100 nA. This value is very low compared to others.
Rating: 1
Range and signal strength
The range is specified with 2 km up to 15 km. In densely populated cities, rather small ranges are achieved due to interference factors such as buildings. On LPWAN standards 34 in the countryside or over open fields, large ranges can be achieved. The signal strength has a sensitivity of -137 dBm, which is ideally suited to penetrate walls and concrete walls. This greatly enhances the availability of sensors and their measurement data.
Rating: 1
Disruptive factors and countermeasures
Due to the frequency spreading, radio signals are transmitted completely, although interference sources may exist. This value can be parameterized and the result evaluated. The sensitivity of -137 dBm helps to compensate for possible existing attenuations.
Rating: 1
IT security and cryptography
For IT security in LoRaWAN, two types of security procedures provide protection against attacks and unauthorized data access. These are over-the-air activation (OTAA) and activation by personalization (ABP). These methods work at the application and network level. At the network level, the authenticity of the deployed device is ensured by a unique ID. At the application level, the application data is protected from the network operator by encryption. Only components that have one of these procedures activated can communicate in a LoRaWAN network.
Rating: 1
Weightless
The Weightless standards are divided into Weightless-W, Weightless-N and Weightless-P. Whereby the development of the standard corresponds to the mentioned order. Weightless-W: Weightless-W is a standard that transmits in TV white space (TVWS). Here, bandwidths that have been set aside by TV broadcasters are used. Transmission takes place in a fixed time slot. In Germany, these frequencies are allocated by the state broadcasting authority.
Weightless-N:
Weightless-N is an ultra-narrow-band transmission technology that builds on the idea of Weightless-W. The network corresponds to the LPWAN typical star-shaped topology. Since the frequencies in Weightless-W are not free, the Weightless-N standard has been developed on the free ISM bands. Frequency hopping, i.e. the controlled and synchronized switching of frequencies, is used for communication. Encryption is performed by 128-bit AES algorithm. Communication is only possible unidirectionally.
Weightless-P:
Builds on the development of Weightless-N and attempts to increase its performance. This standard contains further network functions, such as Forward Error Correction (FEC) and Automatic Retransmission Requests (ARQ). However, communication here is already bidirectional.
Costs and freedoms
The costs for hardware modules and antennas are not clearly defined. The search of stores only delivered individual components. A price comparison of the hardware modules is therefore not possible. Energy efficiency also reduces the maintenance costs here and is comparable to those of LoRaWAN. Weightless-P is a star topology, but it cannot communicate with other nodes as LoRaWAN does, for example. Nevertheless, Weightless-P provides a standard that is not tied to hardware. Rather, the task here is for the enterprise to produce an IoT that fully supports Weightless-P, which can be very costly to develop and manufacture.
Rating: 6
Frequencies and licenses
Weightless-P operates in the license-free spectrum, which is below 1 GHz. In Europe, it is also in the ISM band at 863 MHz. Bidirectional communication is also possible on this frequency, which is important for using the uplink and downlink in Weightless-P and is also advantageous in the scenario.
Rating: 1
Power consumption
The energy consumption in the active state is comparable with other standards. In active mode, however, the parameterized values are decisive for the energy consumption. The advantage with Weightless-P is first of all the transmission speed. For example, the transmission speed is significantly higher than with LoRaWAN, with the same energy requirement. Due to a higher transmission speed, data can be transmitted in a shorter time. As a result, the device is in active mode for a shorter time and thus consumes less energy per transmission of the same data size (depending on how large the amount of data to be transmitted is). In the inactive state, the energy requirement is less than 100000 nA, which is 41 1000 times the LPWAN standard compared to LoRaWAN.
Rating: 4
Range and signal strength
The range in Weightless-P is specified as two kilometers. This range can be achieved in densely populated areas. Larger values for free landscapes are specified with a maximum of five kilometers. At -122 dBm, the sensitivity of the Weightless-P standard is also good against attenuation. The main difference is the significantly higher transmission speed, which is about twice as high as LoRaWAN.
Rating: 4
Disruptive factors and countermeasures
Forward Error Correction and Automatic Retransmission Requests already work against possible error sources. The sensitivity of -122 dBm can work well against hard-to-reach transmitters or receivers. The frequency hopping procedure is also already an integrated measure against third parties who want to listen in, interfere or change data packets in the frequency range.
Rating: 2
IT security and cryptography
128/256-bit AES encryption is used for security. In addition, the nodes used have their own authentication. However, there is a security problem due to the shared key of the nodes. These use the same shared key their entire lifetime. In addition, a session key procedure is completely missing. If the secret (private) key becomes public, no data within this node is safe anymore. The frequency hopping method makes it more difficult for attackers to follow or intercept individual data, since individual bits are sent on different or even multiple carrier frequencies.
Rating: 3
NB-IoT
The NarrowBand-IoT (NB-IoT) is a standard that was published with the 13th release in the 3rd Generation Partnership Project (3GPP) specification. In Germany, this standard is offered by Telekom and Vodafone. The correct designation of the NB-IoT is LTE Cat-NB1. The frequency ranges are to be obtained from the provider as a service. Hardware developed for this purpose must be used for implementation. In principle, the NB-IoT is based on the Long Term Evolution (LTE) network standard, but requires special hardware extensions (modules). Transmissions are made in three different radio spectra, which are differentiated for different requirements.
The switching on and off, of the three operating modes, can be set as required. The frequency range of the licensed LTE frequencies is 700, 800 and 900 MHz. Communication can be bidirectional and it should even be possible to set it up in 2G, 3G, 4G and 5G.
Orthogonal FDMA (OFDMA) for the downlink and single-carrier FDMA (SC-FDMA) for the uplink are used for modulation in the LTE network.
Orthogonal Frequency Division Multiple Access: In this procedure, LPWAN standards 44 broadband signals are converted into narrowband (orthogonal) signals and assigned to the subscriber by multiple access on one or more subcarriers. This corresponds to the implementation of TDMA and FDMA as described in Section 5.4.2, except that the size of the bandwidth can now also be subdivided according to purpose. The method is used in the downlink.
Single-carrier Frequency Division Multiple Access: In SC-FDMA, the data to be transmitted is combined into a group of simultaneously transmitting subcarriers. These subcarrier groups are then regarded as a separate frequency band and transmitted one after the other. For grouping, the data undergoes a discrete Fourier transform, which limits the signals in their spectral characteristics. In simplified terms, these properties can be explained in terms of time domain and frequency domain.
Cost and freedom
The hardware costs can vary for the NB-IoT. The individual communication modules are at the same price level as comparable technologies. The IoTs used behind them can vary, which is why only the modules are mentioned here. The construction of the IoTs with the required special communication modules for the NB-IoT is free.
The use of NB-IoT transmission is purely a service. The largest service providers in Germany are represented by Deutsche Telekom AG (Telekom) and Vodafone Deutschland GmbH (Vodafone).
Rating: 2
Frequencies and licenses
Communication is transmitted in the 700, 800 and 900 MHz frequencies. Providers have licensed various frequency ranges and offer their use as a service. The frequencies in the 700 to 900 MHz range in particular are ideal for network coverage.
Rating: 2
Power consumption
The NB-IoT communication modules have been simplified to such an extent that a battery life of over 10 years is specified. In active mode, power consumption is comparable to other LPWAN technologies such as LoRaWAN. The power consumption in inactive mode is 3000 nA. To keep the power consumption low, CELevel 2 should be avoided.
Rating: 1
Range and signal strength
The achievable range can be adjusted by the CE level. In densely populated areas, coverage of 10 to 15 km can be assumed. However, ranges of up to 25 km are also possible, although these are influenced by CE level 2 and rural areas.
Rating: 1
Disruptive factors and countermeasures
With a sensitivity of -141 dBm, the NB-IoT is well equipped against hard-to-reach receivers. The possibility of increasing the signal strength can also lead to an ideal communication setup, as this is exactly 20 dB above normal LTE with 144 dB with a maximum signal strength of 164 dB. The use of OFDMA and SC-FDMA creates robust and LPWAN standards 47 narrowband transmissions that deliver very high building penetration. Repeated transmission of data packets is an introduced redundancy to protect against information loss.
Rating: 1
IT security and cryptography
Normal LTE, as most people know it, is a communication standard developed by the 3GPP standardization committee. LTE has been under constant development since 2008, and the NB-IoT standard was published in 2016. NB-IoT benefits from already existing and established LTE security functions. These include the authentication available at the end devices, the use of AES as a cryptographic algorithm, and secure key management with integrated key generation.
To authenticate the end devices via a base station to the NB-IoT network, a unique identification number is read out from the respective SIM card of the end device during the first login. This contains a master key K. In the NB-IoT architecture, there is an Evolved Packet System (EPS) that denotes the overall architecture of an LTE system (NB-IoT network). In this there is a Home Subscriber Server (HSS) which is a kind of subscriber database. This also holds the master key K and is used to release permitted services of all terminals registered with the base station. Since the master key K does not start authentication from the terminal device but from the SIM card, the subsequent key exchange is secured against foreign terminals. The SIM cards used are certified by their manufacturers through the GSM Association (GSMA) and also rely on highly secure data centers.
Rating: 1
LTE-M
Long Term Evolution for machines (LTE-M) builds identically to NB-IoT on the LTE network and was also published with the 13th release of the 3GPP specification with an optimization. The architecture of the two LPWAN standards 51 transmission types (NB-IoT and LTE-M) is quite identical. Through a software update, (LTE) base stations can even learn to communicate in the LTE-M network.
Differences to NB-IoT are nevertheless discernible, which also justify the existence of LTE-M. In the areas of transmission speed and latency, the LTE-M is clearly ahead of the NB-IoT. This is due to the bandwidth used. LTE-M operates with a bandwidth of 1.4 MHz, which reflects the smallest radio spectrum in the LTE network. Here, the bandwidth is divided into six resource blocks (RB) of 180 kHz, which are wrapped with a 160 kHz guard band (6 × 180 kHz + 2 × 160 kHz = 1.4 MHz). The modulation of the frequencies is also based on OFDMA and SCFDMA.
Costs and freedoms
With the use of LTE-M, the hardware costs are around 30% higher than with NB-IoT. Furthermore, there are already modules that not only support LTE-M, but whose properties are designed in such a way that they can handle both NB-IoT and LTE-M in version Cat-M1.
Communication via LTE-M is a service provided by providers. In Germany, Telekom and Vodafone are already present and indicate a coverage of 90% [63]. The costs mentioned in Section 5.4.3.1 are to be used for the service. The same SIM cards are used for Telekom as for NB-IoT. The same tariff information can also be seen at Vodafone.
Rating: 2
Frequencies and licenses
Licensed frequency ranges operating in a bandwidth of 1.4 MHz are used for communication in the LTE-M network. Likewise, the introduction of LTE-M Cat-M2 makes it possible to transmit in a bandwidth of 5 MHz. By dividing the bandwidth into smaller frequency bands, better energy efficiency is generated. This method is also used in LTE-M Cat-M2, which means that transmission in a 5 MHz bandwidth also remains power-efficient because transmission times are automatically shorter.
Rating: 2
Power consumption
The battery life of an IoT with LTE-M module is specified as 10 years. This is also achieved by PSM and eDRX. The power consumption in active mode is comparable with other technologies. In inactive mode, the power consumption is slightly higher than with a NB-IoT at about 8000 nA (LTE-M Cat-M1). CE mode B should be avoided to save energy.
Rating: 2
Range and signal strength
The coverage of an LTE-M Cat-M1 is specified with 5 km. The range can be increased a bit by CE mode B. The signal strength is turned up from 144 dB to 156 dB in this case.
Rating: 2
Disruptive factors and countermeasures
In general, the function as already mentioned in the NB-IoT under chapter 5.4.3.5 apply. According to the increase in signal strength triggered by switching to CE mode B, possible improvement can be obtained. However, the intended use depends on whether this mode can or should be applied or not. The sensitivity with -132 dBm also stands for a good penetration rate.
Rating: 1
IT security and cryptography
As with the NB-IoT, IT security is already ensured by various LTE security measures. These therefore also correspond to the procedures mentioned in section 5.4.3.6.
For LTE-M, the mobility function should be mentioned as security against possible failures. Connectivity to the closest mobile cell can reach another mobile cell through movement, as is often the case with cell phones in a train or car. As soon as this promises a shorter or better transmission performance, LTE-M switches to this better cellular cell without losing connectivity. This is a major advantage over NB-IoT, which only has to switch to a new cell by logging off and on again, i.e. re-registering with the mobile network. In the time between logging off and logging on, no connectivity of the NB-IoT is guaranteed.
Rating: 1
EC-GSM-IoT
Extended Coverage GSM IoT (EC-GSM-IoT) is also a communication method developed by the 3GPP specification and was released with the 13th release. Its structure corresponds to that of a GSM network with a modified structure of GPRS called Enhanced-GPRS (eGPRS). EC-GSM-IoT thus operates in the GSM spectrum, but still includes solutions for extended range and energy efficiency. The frequency band is divided into 200 kHz, operating in a bandwidth of 850 to 900 MHz or 1800 to 1900 MHz. Depending on the sampling method, transmission speeds can reach between 70 kbps using Gaussian Minimum Shift Keying (GMSK) or 240 kbps using 8 Phase Shift Keying (8PSK). The TDMA and FDMA methods are combined to modulate the frequency band. Communication can be bidirectional and established in 2G, 3G and 4G.
Costs and freedoms
The cost of a module could not be compared with other technologies because there are none on the market. However, they are said to be cheaper than classic GSM modules.[72] As with NB-IoT or LTE-M, the frequencies are licensed by the providers and their use is offered as a service. In Germany, however, there is no provider that sells SIM cards explicitly for EC-GSM-IoT, let alone offers the service.
Rating: 4
Frequencies and licenses
The frequency range is 850 to 900 MHz and is subject to licensing by each provider if they already support GSM. Communication traffic is limited to machine-to-machine (M2M)/IoT data only. LPWAN standards 56 Machine-to-machine: Pure communication between two devices. Data is limited to sensors and actuators that process it directly or forward it to the communication partner.
Rating: 3
Power consumption
The two methods PSM and eDRX are used for improved energy efficiency. The power consumption should assume a similar value in idle mode, which were already mentioned in the NB-IoT and LTE-M, respectively. The assumption falls back to the fact that the PSM and eDRX methods are also used, as well as the battery lifetime is specified as 10 years, which again coincides with NB-IoT and LTE-M. The cycle times of the eDRX process are also between LTE-M and NB-IoT.
Rating: 2
Range and signal strength
EC-GSM-IoT covers a range of up to 15 km. A signal strength of 164 dB can be achieved. There are two classes for extended coverage. On the one hand, these are specified with 154 dB and have a gain of 23 dBm, and on the other hand with 164 dB with a gain of 33 dBm.
Rating: 1
Disruptive factors and countermeasures
In EC-GSM-IoT, the already known frequency hopping method can be activated, which serves to harden the range. Likewise, the range is scalable and designed with packaging algorithms so that synchronization of the packets can be requested (paging).
Rating: 2
IT security and cryptography
IT security is based on the two processes already mentioned, NB-IoT and LTE-M. This means that an approach based on the LTE network was sought and implemented. This is made up of data authentication, data integrity and data availability.
Nevertheless, there is a risk of DDOS attacks, which is why a Wide-Mouth Frag Protocol (WMFP) protocol could be used.
Wide-Mouth Frag Protocol: The WMFP was developed for insecure mobile networks. It is used against eavesdropping, reply attacks or unauthorized reading of data. The idea is to check generated time stamps for their authenticity. If these can originate from the respective opposite party, the keys for establishing communication are generated and exchanged. If it is detected that the request cannot originate from the correct participant, the keys are neither generated nor are they exchanged. The WMFP can be applied to all cellular IoTs (NB-IoT, LTE-M, EC-GSM-IoT).
Rating: 1
DASH7
The DASH7 method has been developed by the DASH7 Alliance. The protocol operates on license-free ISM bands, with a frequency of 868 MHz for Europe. The network can be set up using a star topology or tree topology.
The DASH7-Alliance-Protocol divides different devices into 4 classes:
Class 1 - Blinker: The Blinker can only send data not receive it.
Class 2 - Endpoint: The endpoint is a typical energy efficient device that can send and receive data. Wake-up events are also supported.
Class 3 - Gateway: The gateway connects a network of endpoints and flashers to another network (gateway). A gateway is never offline and must support all DASH7 functions. It always listens in the network, unless it sends data itself.
Class 4 - Subcontroller: The subcontroller can also support all functions of the DASH7. However, it is not always active. Through wake-up cycles, the device wakes up and performs channel scanning. Push and pull commands are applied for communication. The pull command is similar to a request-response method by which data is exchanged. A push command can only send data in a direction parameterized for it. This is usually done at fixed intervals. The Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA) method, which uses a line scan for collision avoidance, is used to establish communication.
Costs and freedoms
A gateway module is quoted at around 150 € and can be obtained from Wizzilab. A simple flasher is available for 89 €. If you roughly compare these figures with the functions of the individual devices, they can be compared with modules from LoRa. However, LoRa offers a much wider range of modules and sensors. The modules that can be obtained from Wizzilab also handle LoRa. The DASH7 Alliance protocol is publicly available and free, so only private networks are possible. Since it works with the free frequencies, the only costs are hardware acquisition and network maintenance. The communication is bidirectional.
Rating: 1
Frequenzen und Lizenzen
The frequencies used are at 868 MHz in Germany and are not subject to any license. Nor are licenses claimed by the DASH7 Alliance. Just as with LoRaWAN, the frequencies 915 MHz are used in North America and 433 MHz in Asia.
Rating: 1
Power consumption
With an average power consumption of 30000 nA, the energy efficiency is relatively good. The power consumption in the inactive state is very low at 4000 nA, but somewhat higher for comparison with LoRaWAN. The power consumption also differs greatly depending on the modules used. LPWAN standards 60 Because a gateway is always active and listening in the network with DASH7, it should rather receive its own power supply.
Rating: 3
Range and signal strength
The range is specified as up to 5 km [35]. The DASH7 Alliance also sees its range more in the medium coverage and especially in areas with 500 m range. The signal strength has a sensitivity of -110 dBm, which is also suitable for penetrating walls and concrete walls. However, this is only possible at a small range such as up to 500 m. The power transmission balance is 140 dB.
Rating: 6
Disruptive factors and countermeasures
There is a frequency hopping procedure, but this is limited to only two frequencies. The CSMA/CA method is used for collision-free transmission in the network. The signal strength and power transmission balance are sufficient for small ranges.
Rating: 4
IT security and cryptography
DASH7 uses symmetric AES encryption for confidentiality and authentication in the communication network. The secret key is stored in a node file and remains there until the end of the subscriber's life.
Rating: 3
Final assessment and summary of findings
In the first step, five of the six evaluations of each LPWAN standard are summarized and an average value is calculated. These are made up of the criteria:
• Costs and freedoms,
• Frequencies and licenses,
• power consumption,
• range and signal strength,
• Interference factors and countermeasures.
In the second step, a table is drawn up with the mean value formed and the remaining criterion, and then the two best LPWAN standards are named.
Averaging for assessment
Table 3 now lists the individual ratings of the respective LPWAN standards based on the five criteria included, and the resulting mean value is shown in the last column.
Table 3: Averaging of five of the six criteria
-LPWAN Standards
| Costs & Freedoms | Frequencies & Licenses | Power consumption | Range & Signal Strength | Disruptive factors & countermeasures |
Average
|
LoRa / LoRaWAN |
1 |
1 |
1 |
1 |
1 |
1 |
Weightless | 6 | 1 | 4 | 4 | 2 | 3,4 |
NB-IoT | 2 | 2 | 1 | 1 | 1 | 1,4 |
LTE-M | 2 | 2 | 2 | 2 | 1 | 1,8 |
EC-GSM-IoT | 4 | 3 | 2 | 1 | 2 | 2,4 |
DASH7 | 1 | 1 | 3 | 6 | 4 | 3 |
It can be seen from the table that the LPWAN standards LoRaWAN, NB-IoT and LTE-M clearly stand out from the rest of the standards. Nevertheless, in the next table all LPWAN standards are evaluated with their determined mean value and the criterion:
• IT security and cryptography. The mean value from these evaluation points is taken as the result and final assessment.
Final assessment
The penultimate column of the table now lists the final result of the assessment of all the LPWAN standards considered. The last column serves to clearly show which rank the respective standard has achieved.
Table 4: Final result of all criteria
LPWAN- Standards |
Average
| IT Security & Cryptography |
Final result
| Rank |
LoRa / LoRaWAN |
1 |
1 |
1 |
1 |
Weightless | 3,4 | 3 | 3,2 | 6 |
NB-IoT | 1,4 | 1 | 1,2 | 2 |
LTE-M | 1,8 | 1 | 1,4 | 3 |
EC-GSM-IoT | 2,4 | 1 | 1,7 | 4 |
DASH7 | 3 | 3 | 3 | 5 |
The final result is LoRa/LoRaWAN in first place, closely followed by NB-IoT in second place and LTE-M in third place. All other LPWAN standards are far behind or so poorly represented on the market that their deployment cannot materialize (EC-GSM-IoT).
Summary of the findings
The LPWAN standards examined in this paper can be divided into two groups. The standards with free frequencies, which are not subject to a license and are also completely independent of service providers, form group one. Group one thus includes LoRa/LoRaWAN, Weightless and DASH7. In this group, LoRa/LoRaWAN has a clear lead and is also ahead of the second group, especially according to this assessment. The second group includes LPWAN standards that do not use free frequencies and whose network is offered as a service by various providers. In this group, the NB-IoT standard leads, just ahead of LTE- LPWAN standards 64 M and is just behind LoRa/LoRaWAN. The EC-GSM-IoT standard is somewhat behind. This is mainly due to the uncertainty of whether or not the 2G network may be shut down in the next few years. Likewise, there is no supply on the market.
LoRa/LoRaWAN and NB-IoT are recommended from the final evaluation for LPWAN network deployment. LoRaWAN offers the possibility to build his own network. This means everyone is responsible for their own network. Advantages can be cost savings, because there are no monthly fees. There are only hardware costs and maintenance costs for the network. However, if the network is difficult or cost negative to implement, the NB-IoT option should be considered. Here, an existing network of a provider could provide coverage that would be more suitable than LoRa/LoRaWAN from a purely economic point of view. Accordingly, only the service provider has to take care of the network, which in turn leads to constant costs due to monthly fees. The maintenance costs of the network would thus also fall into monthly fees. But LTE-M could also find its areas of application. Especially in terms of mobility, this standard is a step ahead of all others. Likewise, when it comes to latency or transmission speed, this standard would be more worthwhile compared to the other two.
The other two are more likely to be used for stationary installations. Since the location does not change once the systems are installed, mobility is also not an issue. For the water supply scenario under consideration, however, the LPWAN standards LoRa/LoRaWAN and NB-IoT remain the first choice. The IT security of the LPWAN standards mentioned is rated as very good, which means that the use of both of them, and also of LTE-M, is to be advocated. For security, the LPWAN standards LoRa/LoRaWAN, NB-IoT and LTE-M already have a lot of features. Most of them serve to ensure the protection goals formed by availability, integrity and confidentiality.
Sources used:
[1] P. Schnabel: LPWAN – Low Power Wide Area Network,https://www.elektronik-kompendium.de/sites/kom/2207181.htm, Retrieved 05.01.2021.
[2] Waldemar Heinrich, M.Eng.: Masterarbeit „Evaluierung von LPWAN-Standards, deren IT-Sicherheitsanforderungen und technischen Designs zur Integration in ein geplantes Smart Water Grid“, Kapitel 5
[3] M. Linnemann, A. Sommer und R. Leufkes: Einsatzpotentiale von LoRaWAN in der Energiewirtschaft: Praxisbuch zu Technik, Anwendung und regulatorischen Randbedingungen, Wiesbaden Deutschland: Springer Vieweg, 2019.
[4] R. Koning: Smart City – Made in Germany, Wiesbaden Deutschland: Springer Nature, 2020.
[5] B. Ray, slideshare: LPWAN Cost Webinar, 06.07.2017,https://www.slideshare.net/BrianRay10/lpwan-sost-webinar, Retrieved am 23.06.2021.
[6] Elektronik Kompendium: LoRa/LoRaWAN – Long Range Wide Area Network,https://www.elektronik-kompendium.de/sites/kom/2203171.htm, Retrieved am 23.06.2021.
[7] C. Anselmi, Antevorte: NB-IoT oder LTE Cat M1 – Teil 1 / Energieverbrauch?, 28.02.2021,https://antevorte.biz/nb-iot-oder-lte-cat- m1-teil1-energieverbrauch/, Retrieved am 23.06.2021.
[8] Fernauslese: Funkübertragung mit LoRa,https://fernauslese.de/kommunikation/lora/, Retrieved am 23.06.2021.
[9] B. Foubert und N. Mitton: Long-Range Wireless Radio Technologies: A Survey, Basel Schweiz: MDPI, 2020.
[10] Weightless-P Systemspecifications Version 1.03:https://pro-bee-user- content-eu-west-1.s3.amazonaws.com/public/users/Integrators/929cb090- e779-401a-b06c-c629ff6b0fea/ap-cambridgestartuplimi/Weightless- P_v1.03.pdf, 2017, Retrieved am 26.06.2021. S. 27.
[11] B.S. Chaudhari und M. Zennaro: LPWAN Technologies for IoT and M2M Applications, Chennai Indien: Academic Press, 2020. S.119-135, S. 159-151.
[12] TechTarget: LPWAN (Low-Power Wide Area Network),https://www.computerweekly.com/de/definition/LPWAN-Low-Power-Wide- Area-Network, Retrieved am 26.04.2021.
[13] B. Ray, Link Labs: What is Weightless?,https://www.link- labs.com/blog/what-is-weightless, 2015, Retrieved am 25.06.2021.
[14] M. Patrick, elektroniknet: Auswahl des richtigen Übertragungs-Protokolls,https://www.elektroniknet.de/automation/auswahl-des-richtigen- uebertragungs-protokolls.176835.html, Retrieved am 25.06.2021.
[15] Ubik: What is Weightless-P?, 21.09.2016,https://www.ubiik.com/post/2016/09/21/what-is-weightless-p, Retrieved am 26.06.2021.
[16] G.Pathak, J. Gutierrez und S. Ur Rehman: Security in Low Powered Wide Area Networks: Opportunities for Software Defined Network-Supported Solutions, Basel Schweiz: MDPI, 2020. S.2-3.
[17] ITWissen: FDMA-Verfahren,15.10.2013,https://www.itwissen.info/OFDMA-orthogonal-frequency-division-multiple- access.html, Retrieved am 26.06.2021.
[18] LNTwww: Anwendung von OFDMA und SC-FDMA in LTE, 05.03.2021,https://www.lntwww.de/Mobile_Kommunikation/Anwendung_von_OFDMA_und_SC-FDMA_in_LTE, Retrieved am 03.07.2021.
[19] LNTwww: Diskrete Fouriertransformation (DFT), 14.05.2021,https://www.lntwww.de/Signaldarstellung/Diskrete_Fouriertransformation_( DFT), Retrieved am 03.07.2021.
[20] Ioteasyconnect: Vodafone Business IoT Easy Connect NB-IoT, 16.10.2020,https://www.ioteasyconnect.de/assets/download/iot-easy- connect-nb-iot.pdf, Retrieved am 06.07.2021.
[21] Smart-connect-shop.iot.telekom: Bestellübersicht,https://smart-connect- shop.iot.telekom.com/tdg-shop/shop/cart, Retrieved am 06.07.2021.
[22] B. S. Chaudhari, M. Zennaro und S. Borkar, LPWAN Technologie: Emerging Application Characteristics, Requirements, and Design Considerations, Basel Schweiz: MDPI, 2020.
[23] Deutsche Telekom AG: NB-IoT, LoRaWAN, Sigfox: ein aktueller Vergleich, 04.2021,https://iot.telekom.com/resource/blob/data/570954/0ddb2c4808e68427035 d415001fc645d/mobile-iot-netzwerk-vergleich-nb-iot-lorawan-sigfox.pdf, Retrieved am 06.07.2021.
[24] H. Naumann und S. Human, Industry of things: LPWAN im Vergleich zu SubGHz Meshnet, 17.08.2020,https://www.industry-of-things.de/lpwan- im-vergleich-zu-subghz-meshnet-a-955306/, Retrieved am 07.07.2021.
[25] S. Tabbane, ITU: Session 5: NB-IoT Networks, Microsoft PowerPoint - Session 5_NB-IoT Networks.pptx (itu.int), Retrieved am 07.07.2021.
[26] Businessblog.magenta: NarrowBand-IoT (NB-IoT),https://businessblog.magenta.at/narrowband-iot, Retrieved am 07.07.2021.
[27] Deutsche Telekom AG: Vergleich und Analyse der Sicherheitsaspekte von LoRaWAN und NB-IoT, 04.2021,https://iot.telekom.com/resource/blob/data/584120/c9330ff11895ec32c4eb 30b9c86f0e15/sicherheitsaspekte-lorawan-nb-iot.pdf, Retrieved am 07.07.2021.
[28] J. Köpp, ROHDE & SCHWARZ: Einblicke in LTE-M gemäß 3GPP Release 14, 03.09.2018,https://www.rohde-schwarz.com/de/knowledge- center/videos/einblicke-in-lte-m-gemaess-3gpp-release-14-video- detailseite_251220-575809.html, Retrieved am 13.07.2021.
[29] Telit: ME910C1 Series Datasheet, 03.2021, Telit_ME910C1_Datasheet.pdf (netdna-ssl.com), Retrieved am 13.07.2021.
[30] GSMA: Security Features of LTE-M and NB-IoT Networks, 27.09.2019, Security-Features-of-LTE-M-and-NB-IoT-Networks.pdf (gsma.com), Retrieved am 15.08.2021.
[31] GSMA: LTE-M deployment guide to basic feature set requirements, 06.2019, 201906-GSMA-LTE-M-Deployment-Guide-v3.pdf, Retrieved am 13.07.2021.
[32] Y.Kabalci und M. Ali: Emerging LPWAN Technologies for Smart Environments: An Outlook, 2019,https://www.semanticscholar.org/paper/Emerging-LPWAN-Technologies- for-Smart-Environments%3A-Kabalci- Ali/80c07adde097633e0eaa8fc086db6a0bbea8732d, Retrieved am 13.07.2021.
[33] GSMA: 3GPP Low Power Wide Area Technologies, 05.2018,https://www.gsma.com/iot/wp-content/uploads/2018/05/3GPP-Low-Power- Wide-Area-Technologies-GSMA-White-Paper.pdf, Retrieved am 26.07.2021.
[32] ITWissen: Maschine-zu-Maschine-Kommunikation, 21.08.2020,https://www.itwissen.info/M2M-machine-to-machine-Maschine-zu- Maschine-Kommunikation.html, Retrieved am 26.07.2021.
[33] 3GPP: Work-Plan, 09.2019,https://www.3gpp.org/ftp/Information/presentations/presentations_2019/Po ster_2019_08_v7_optimized.pdf, Retrieved am 26.07.2021.
[34] Embedded: Cellular IoT – Comparison of CIoT technologies, 15.10.2018,https://www.embedded.com/cellular-iot-comparison-of-ciot-technologies/, Retrieved am 26.07.2021.
[35] ETSI: Technical specifikation, 08.2017,https://www.etsi.org/deliver/etsi_ts/145000_145099/145001/14.02.00_60/t s_145001v140200p.pdf, Retrieved am 26.07.2021.
[36] R. Selvaraj, V.M. Kuthadi, S. Baskar, P. M. Shakeel und A. Ranjan: Creating Security Modelling Framework Analysing in Internet of Things Using EC-GSM-IoT, 29.06.2021,https://link.springer.com/content/pdf/10.1007/s13369-021-05887-y.pdf, Retrieved am 26.07.2021.
[37] ITWissen: Dash7,11.11.2020,https://www.itwissen.info/Dash7- Dash7.html, Retrieved am 24.07.2021.
[38] M. Weyn, G. Ergeerts, L. Wante, C. Vercauteren und P. Hellinckx: Survey of the DASH7 Alliance Protocol for 433MHz Wireless Sensor Communication,https://www.researchgate.net/publication/259389031_Survey_of_the_DAS H7_Alliance_Protocol_for_433_MHz_Wireless_Sensor_Communication, Retrieved am 26.07.2021.
[39] WIZZILAB: Shop,https://wizzilab.com/shop, Retrieved am 27.07.2021.
[40] M2Mgermany: Shop LoRa Sensors,https://www.m2mgermany.de/shop/produkte/lora- sensors/?gclid=EAIaIQobChMIrdOSqviD8gIVFZ_VCh2wPwffEAAYAiAAE gJpqfD_BwE, Retrieved am 27.07.2021.
[41] DASH7 Alliance:https://dash7-alliance.org/, Retrieved am 27.07.2021.
[42] W. Ayoub, A. Samhat, F. Nouvel, M. Mroue und J.C. Prévotet: Internet of Mobile Things: Overview of LoRaWAN, DASH7, and NB-IoT in LPWANs standards and Supported Mobility, 23.10.2018, Internet of Mobile Things: Overview of LoRaWAN, DASH7, and NB-IoT in LPWANs standards and Supported Mobility (archives-ouvertes.fr), Retrieved am 27.07.2021.
[43] J. Norair: Introduction to DASH7 Technologies, 16.03.2009, 269.pdf (rfidjournal.com), Retrieved am 28.07.2021.
[44] O. Cetinkaya und O.B. Akan: A DASH7-based Power Metering System, 01.2015,https://www.researchgate.net/publication/308855116_A_DASH7- based_power_metering_system, Retrieved am 28.07.2021.